

Our Guarantees Our Quality Standards Our Fair Use Policy
What Makes UK Essays Different?
- We have a verifiable trading history as a UK registered company (details at the bottom of every page).
- Our Nottingham offices are open to the public where you can meet our team of over 40 full-time staff.
- UK Essays partner with Feefo.com to publish verified customer testimonials – both good and bad!
Ask an Expert FREE
Ask an Expert Index Ask a Question Paid Services
About Our Ask an Expert Service
Our totally free “Ask an Expert” Service allows users to get an answer of up to 300 words to any academic question.
- Questions typically answered within 24 hours.
- All answers are researched and written by fully qualified academics in the question’s subject area.
- Our service is completely confidential, only the answer is published – we never publish your personal details.
- Each professional answer comes with appropriate references.
About Us
More About Us
Published: 23, March 2015
In recent years the prevalent area of research is in the field of MANET because of the challenges they pose to protocols. MANET is a new technology in which users communicate without any fixed physical infrastructure. So, MANET is also referred to as an infrastructure-less network. MANET has become a fastest growing network as it is cheap, small and because of its powerful devices. An ad-hoc network is self-organizing and adaptive. Devices in mobile ad-hoc network should be able to detect the presence of other devices and perform necessary set-up to facilitate communication and sharing of data and service. Ad-hoc networking allows the devices to maintain connections to the network as well as easily adding and removing devices to and from the network.


In MANET, set of applications is diverse which ranges from large-scale, mobile and highly dynamic network to small static networks which are constrained by power sources. Besides the legacy applications that enter into an ad hoc context from the traditional based infrastructure environment, new services will be generated for the new environment which includes: Sensor Networks, Military Battlefield, Medical Service and Personal Area Network. The most important concern is the security in Mobile Ad Hoc Network for its basic functionality. By ensuring that the security issues have been met, the integrity and confidentiality of the data and also the availability of network services can be achieved. Because of some of the features of MANET like lack of central monitoring and management, cooperative algorithms, open medium, changing its topology dynamically and no clear defense mechanism MANET suffer from security attacks. The battle field situation for the MANET have been changed by these factors against the security threats
Professional
Get your grade
or your money back
using our Essay Writing Service!
Essay Writing Service
The thesis contributes to the subject area of problems and prospects of Mobile Ad Hoc Network. It is mainly focussed on the study and analysis of security issues and security solutions of MANET, especially for those selecting sensitive applications, have to meet the following design goals while addressing the above challenges.
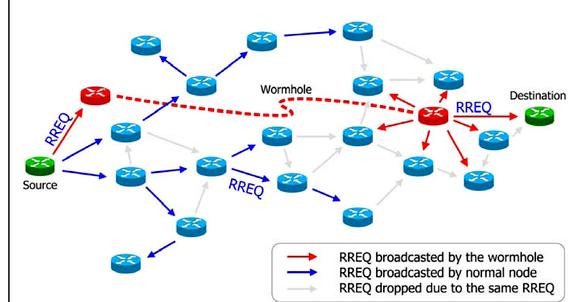
MANET is more vulnerable than wired network due to mobile nodes, threats from compromised nodes inside the network, limited physical security, dynamic topology, scalability and lack of centralized management. Because of these vulnerabilities, MANET is more prone to malicious attacks. The primary focus of this work is to provide a survey on various types of attacks that affect the MANET behaviour due to any reason.
Motivation
MANET is an active area of research and also an emerging field. These networks find application in various scenarios like disaster relief to military services and task forces to emergency operations. In such scenarios providing security is very critical. The limitation of the MANET is the limited resource capability: bandwidth, power backup and computational capacity. The security of MAENT is difficult due to dynamically changing topology, absence of infrastructure, vulnerability of channels and nodes. Also, for monitoring the network operations no central authority is present. So the security schemes for wire networks cannot be used in MANET, Which would make them more vulnerable to attacks.
To secure a wireless ad-hoc network is a very challenging issue. To develop good security solution the first step is to understand the possible forms of attacks. For secured transmission of information the security of communication in MANET is very important. MANET becomes more vulnerable to cyber/digital attacks than the wired network due to the absence of a central co-ordination mechanism and shared wireless medium.
Objectives
The primary objective of this work can be summarized as follows:
To study the existing mobile ad-hoc network and its services in different scenarios;
To study the performance of ad-hoc routing protocols and its behaviour;
To study and focus on the analysis of the Routing Misbehaviour in MANET and its consequences;
To analyse the effects of black hole attacks, flooding attacks and wormhole attacks in the light of network load, throughput and end-to-end delay in MANET;
To simulate black hole attacks, flooding attacks and wormhole attacks using different Reactive Routing Protocols;
To compare the results of different Reactive Protocols to analyse which of these protocols are more vulnerable to these attacks; and
To suggest previously proposed plans for counter measurement of these attacks.
Methodology
Our Guarantees Our Quality Standards Our Fair Use Policy
What Makes UK Essays Different?
- We have a verifiable trading history as a UK registered company (details at the bottom of every page).
- Our Nottingham offices are open to the public where you can meet our team of over 40 full-time staff.
- UK Essays partner with Feefo.com to publish verified customer testimonials – both good and bad!
Ask an Expert FREE
Ask an Expert Index Ask a Question Paid Services
About Our Ask an Expert Service
Our totally free “Ask an Expert” Service allows users to get an answer of up to 300 words to any academic question.
- Questions typically answered within 24 hours.
- All answers are researched and written by fully qualified academics in the question’s subject area.
- Our service is completely confidential, only the answer is published – we never publish your personal details.
- Each professional answer comes with appropriate references.
About Us
More About Us
Published: 23, March 2015
In recent years the prevalent area of research is in the field of MANET because of the challenges they pose to protocols. MANET is a new technology in which users communicate without any fixed physical infrastructure. So, MANET is also referred to as an infrastructure-less network. MANET has become a fastest growing network as it is cheap, small and because of its powerful devices. An ad-hoc network is self-organizing and adaptive. Devices in mobile ad-hoc network should be able to detect the presence of other devices and perform necessary set-up to facilitate communication and sharing of data and service. Ad-hoc networking allows the devices to maintain connections to the network as well as easily adding and removing devices to and from the network.
In MANET, set of applications is diverse which ranges from large-scale, mobile and highly dynamic network to small static networks which are constrained by power sources. Besides the legacy applications that enter into an ad hoc context from the traditional based infrastructure environment, new services will be generated for the new environment which includes: Sensor Networks, Military Battlefield, Medical Service and Personal Area Network. The most important concern is the security in Mobile Ad Hoc Network for its basic functionality. By ensuring that the security issues have been met, the integrity and confidentiality of the data and also the availability of network services can be achieved. Because of some of the features of MANET like lack of central monitoring and management, cooperative algorithms, open medium, changing its topology dynamically and no clear defense mechanism MANET suffer from security attacks. The battle field situation for the MANET have been changed by these factors against the security threats
Professional
Get your grade
or your money back
using our Essay Writing Service!
Essay Writing Service
The thesis contributes to the subject area of problems and prospects of Mobile Ad Hoc Network. It is mainly focussed on the study and analysis of security issues and security solutions of MANET, especially for those selecting sensitive applications, have to meet the following design goals while addressing the above challenges. MANET is more vulnerable than wired network due to mobile nodes, threats from compromised nodes inside the network, limited physical security, dynamic topology, scalability and lack of centralized management. Because of these vulnerabilities, MANET is more prone to malicious attacks. The primary focus of this work is to provide a survey on various types of attacks that affect the MANET behaviour due to any reason.
Motivation
MANET is an active area of research and also an emerging field. These networks find application in various scenarios like disaster relief to military services and task forces to emergency operations. In such scenarios providing security is very critical. The limitation of the MANET is the limited resource capability: bandwidth, power backup and computational capacity. The security of MAENT is difficult due to dynamically changing topology, absence of infrastructure, vulnerability of channels and nodes. Also, for monitoring the network operations no central authority is present. So the security schemes for wire networks cannot be used in MANET, Which would make them more vulnerable to attacks.
To secure a wireless ad-hoc network is a very challenging issue. To develop good security solution the first step is to understand the possible forms of attacks. For secured transmission of information the security of communication in MANET is very important. MANET becomes more vulnerable to cyber/digital attacks than the wired network due to the absence of a central co-ordination mechanism and shared wireless medium.
Objectives
The primary objective of this work can be summarized as follows:
To study the existing mobile ad-hoc network and its services in different scenarios;
To study the performance of ad-hoc routing protocols and its behaviour;
To study and focus on the analysis of the Routing Misbehaviour in MANET and its consequences;
To analyse the effects of black hole attacks, flooding attacks and wormhole attacks in the light of network load, throughput and end-to-end delay in MANET;
To simulate black hole attacks, flooding attacks and wormhole attacks using different Reactive Routing Protocols;
To compare the results of different Reactive Protocols to analyse which of these protocols are more vulnerable to these attacks; and
To suggest previously proposed plans for counter measurement of these attacks.
Methodology
Previous answers to this question
This is a preview of an assignment submitted on our website by a student. If you need help with this question or any assignment help, click on the order button below and get started. We guarantee authentic, quality, 100% plagiarism free work or your money back.
 Get The Answer
Get The Answer